Jump To: Support > KB > NetManager > VPN > Server > Config
VPN Server - Configuration in detail
The configuration page consists of a number of sections. Each section has explanatory notes underneath it, but here we have separated the page out to explain about each option in order. We've started from the second field as the first field is just to enable/disable the VPN.
Port Number

The VPN server will listen on a certain port.The default port number is 1194 which is globally assigned by IANA for OpenVPN. However, virtually any port can be chosen as long as it is not used for any other service (so for example, you cannot choose port 80 as this is used by the webserver). Being able to alter the port is useful if you have a locked down Internet connections with very limited access to open ingoing ports. For example, some Internet providers are happy to open port 1935 (Macromedia Flash Communications Server) even if they refuse to open 1194.
Port 443 is a special-case. It is normally used by HTTPS (secure web services). If you set the VPN server to use port 443 (with protocol TCP), it will transparently share the port with the webserver meaning that users with a web-browser will see your webpages as usual, but VPN clients will be able to connect too.
N.B. Changing this value later on will mean altering the port number in all your client configuration files.
Protocol

Here you can select the most appropriate protocol to use. If possible, you should use UDP as it will give lower latency on your VPN (particularly important if you want to run things like VoIP). However, in the same way as selecting a port, you may be limited by your Internet provider if they provide an overly restrictive service.
N.B. Changing this value later on will mean altering the protocol in all your client configuration files.
Hostname
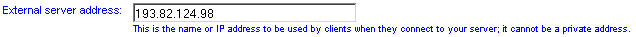
Enter here the external host name or IP address that you will use to connect to this server from your VPN client machines. This is used to generate the client configuration files only - it does not affect the server configuration.
Client-to-client
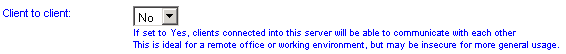
If Client-to-Client connections are allowed, each client computer that connects will be able to see all the others as well as the NetManager and the local network. Depending on your needs, you may consider this to be a security problem (potentially one client could attack another). On the other hand, it can be extremely useful if you have multiple sites linked together.
Compression
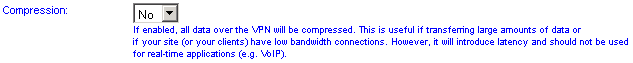
For general use compression can be enabled (the actual data going over the VPN is checked and if it cannot be compressed, the VPN server will automatically switch off compression for a period).
If your Internet connection is fast or it is important that the data is transferred as quickly as possible (e.g. if using VoIP), then you can force compression off.
Inline configuration
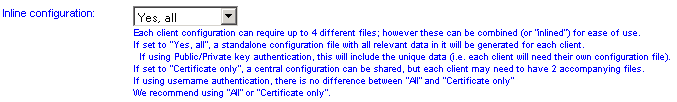
The client configuration (when using public/private keys) consists of 4 different components (the configuration file, the server verification certificate, the client certificate and the private key). This option should usually be left at the default setting of Yes, all which includes all 4 components in a single configuration file.
VPN Network range
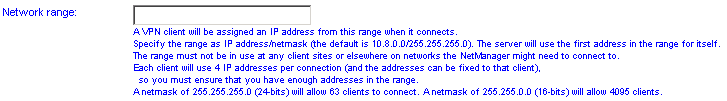
When client computers connect, they will be given an IP address from the range configured here. With Windows clients this will allow up to 64 different client machines to be connected at any one time (though see the Persistent addresses option below).
It is generally fine to use the default, but you will need to change it if it would not provide enough connections or clashed with any network ranges locally or that your VPN client machines will be using.
Persistent Addresses
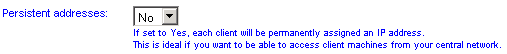
If this option is enabled, every time a client computer connects it will be allocated the same IP address (from the range above). This is very useful if you want to connect to resources on a VPN client machine and thus need to know its address (for example, if your home PC is connected and you wish to connect to it with Remote Desktop).
You should bear in mind that because IP addresses will not be re-used, you may need a bigger number of addresses.
Authentication Method
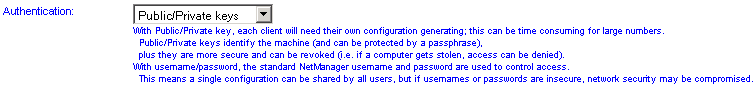
You will generally configure this option based on a balance between your security concerns and ease of use. Public/private keys are the safest to use but this will require an administrator to generate a new configuration file for each user. For more details, please see the Overview section at the top of the page.
Allowed Users and Groups
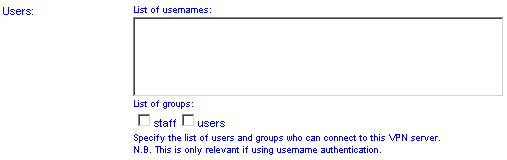
If you have selected user authentication you must specify the users/groups that you wish to grant access to.
<<< Return to the overview | Forward to per-client configuration >>>





