Jump To: Support > KB > NetManager > Firewalling > PortMapping
Port Mapping
At its simplest, port mapping allows you to forward connections made to the NetManager onto other machines. This means you only need a small number of external IP addresses (usually just one) for allowing access to machines from the outside. This access can, of course, be firewalled. It should not be confused with Reverse Proxying.
It can be configured in Network > NAT in webadmin.
As an example, look at the configuration below:
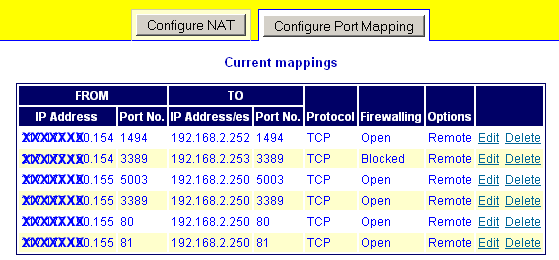
The left column is the external IP address (obscured for security). Two IP addresses are used in this case (i.e. the NetManager has Aliased addresses. In this example, it is necessary to use more than one IP address as port 80 is mapped through to an internal machine; if only a single IP address was used, this would stop access to the NetManager's webserver. On a port-by-port basis, these are mapped through to 3 different internal machines. Firewalling is controlled individually for each mapping.
Each mapping can be configured as remote or local. Remote will not be available if you are not using NAT. In remote mode, the NetManager firewall remaps the traffic transparently. The internal machine will see the traffic as coming from its original (external) IP address. Therefore, the internal target machine must have its default gateway set to the NetManager. In local mode, the NetManager will accept the incoming connection itself and then open a new connection to the internal machine. This means that the internal target machine will see the traffic as coming from the NetManager, not the original address. It also places slightly more load on the NetManager.
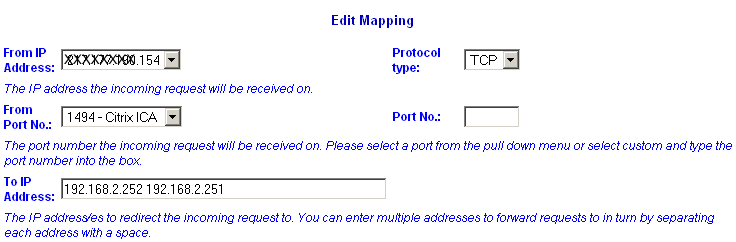
Round-robin mapping
More than one destination IP address can be specified. This will allow 'round-robin' access (i.e. each IP address will be used in turn) - this gives crude load balancing. In the example below, the top rule (port 1494) is being edited to add a second IP address.
Advanced operations
Port mapping settings are defined in/etc/netmanager/nat.rdr. This consists of a series of lines in the following format:FROM_IP FROM_PORT[,FROM_OPTS] TO_IP TO_PORT [RESTRICT] [LOCAL]
- FROM_IP = IP address to map from. This will usually be an IP address on this server, but can be any address or network (specified in CIDR network/bits format). If it is not an address on the server, the network interface to intercept on must be specified as an option (see below). Set to
anyto listen on all ports (forces a local redirect, see LOCAL below) - FROM_PORT = port number to intercept. Set to
allto map all ports (a bimap redirection). Set to a comma-separated list to map to the corresponding port from the same length list for TO_PORT. If port ends inu, map UDP otherwise map TCP - FROM_OPTS = additional options separated by commas. Supported options are:
- ssl=CERTIFICATE = set up an SSL server with specified certificate. Not supported unless LOCAL is set to local
- int=INTERFACE = map from specified interface. Only necessary if FROM_IP is not a local address on this server
- TO_IP = IP address to redirect traffic to (must be on a locally-attached network). If a comma-separated list, then round-robin will be used (if applicable)
- TO_PORT = port to redirect traffic to
- RESTRICT = comma-separated list of IP addresses to allow connections from. If empty or set to
any, all IP address will be able to connect - LOCAL = if set to
local, the traffic will be forwarded from a local IP address on this server, otherwise the original source IP address will be kept





